OpenVPN server (debian,ubuntu,kali,raspberry pi) + IOS13 – IOS16 client
Update: this is still working on December 2023 with IOS16
apt install openvpn easy-rsa
cp -r /usr/share/easy-rsa /etc/openvpn/
cd /etc/openvpn/easy-rsa
vim vars/etc/openvpn/vars content
export KEY_COUNTRY="Serbia"
export KEY_PROVINCE="RS"
export KEY_CITY="Belgrade"
export KEY_ORG="LinuxWin"
export KEY_EMAIL="[email protected]"
export KEY_OU="OpenVPN"Initialize PKI
./easyrsa init-pkiBuild the CA without a password
./easyrsa build-ca nopassGenerate the server key
./easyrsa gen-req server nopassSign the server certificate
./easyrsa sign-req server serverBuild a Diffie-Hellman key exchange
./easyrsa gen-dhGenerate a HMAC signature
openvpn --genkey --secret ta.keyCopy all the certificate and key to the /etc/openvpn
cp ta.key /etc/openvpn/
cp pki/ca.crt /etc/openvpn/
cp pki/private/server.key /etc/openvpn/
cp pki/issued/server.crt /etc/openvpn/
cp pki/dh.pem /etc/openvpn/Generate Client certificate
./easyrsa gen-req client nopassSign Client certificate
./easyrsa sign-req client clientCopy client certificate and key to /etc/openvpn/client/
cp pki/ca.crt /etc/openvpn/client/
cp pki/issued/client.crt /etc/openvpn/client/
cp pki/private/client.key /etc/openvpn/client//etc/openvpn/server.conf file
port 1194
proto udp
dev tun
ca /etc/openvpn/ca.crt
cert /etc/openvpn/server.crt
key /etc/openvpn/server.key # This file should be kept secret
dh /etc/openvpn/dh.pem
;dh none
server 192.168.10.0 255.255.255.0
push "redirect-gateway def1 bypass-dhcp"
push "dhcp-option DNS 8.8.8.8"
push "dhcp-option DNS 208.67.220.222"
keepalive 10 120
;tls-auth ta.key 0 # This file is secret
tls-crypt /etc/openvpn/ta.key 0
auth SHA256
cipher AES-256-GCM
user nobody
group nogroup
persist-key
persist-tun
tun-mtu 1500
status /var/log/openvpn/openvpn-status.log
log /var/log/openvpn/openvpn.log
log-append /var/log/openvpn/openvpn.log
verb 3
explicit-exit-notify 1enable IP forwarding
vim /etc/sysctl.conf
###uncoment following line###
net.ipv4.ip_forward=1
###save and exit###
sysctl -p
### the other way is to do the same ###
echo 1 > /proc/sys/net/ipv4/ip_forwardFirewall rules
### for server behind NAT ###
iptables -t nat -A POSTROUTING -o eth0 -j MASQUERADE
### or just...###
iptables -t nat -A POSTROUTING -j MASQUERADE
### open udp port 1194 ###
iptables -A INPUT -i eth0 -m state --state NEW -p udp --dport 1194 -j ACCEPT
### allow TUN interface ###
iptables -A INPUT -i tun0 -j ACCEPT
iptables -A FORWARD -i tun0 -j ACCEPT
To save rules to be loaded on boot install iptables-persistent
sudo apt install iptables-persistent
### current iptables rules will be saved to the
### /etc/iptables/rules.v4
### /etc/iptables/rules.v6Start OpenVPN server service
systemctl start openvpn@server
### check status with..###
systemctl status openvpn@server.ovpn config file for ios
client
dev tun
proto udp ####tcp if you use tcp protocol
remote 192.168.100.55 ### your server ip address or domain
port 1194 ####1194 only if your vpn server's port is the default port
resolv-retry infinite
nobind
persist-key
persist-tun
tun-mtu 1500
;link-mtu 1549
mssfix 1300
auth SHA256
;auth-user-pass
verb 5
;comp-lzo ###(disable compression)
remote-cert-tls server
cipher AES-256-GCM
redirect-gateway def1
;remote-gateway 192.168.6.1
;dhcp-options DNS .8.8.8.8
;route 192.168.6.0 255.255.255.0 192.168.6.1
<ca>
ca.crt ### copy content here ###
</ca>
<cert>
clinet.ctr ### copy content here ###
</cert>
<key>
client.key ### copy content here ###
</key>
<tls-crypt>
ta.key ### copy contet of ta.key here ###
</tls-crypt>
Import .ovpn config file to ios via itunes, mail, google drive, onedrive…
There is a little script I made to automate this last step, (generate config file with all certificates). OVPNconfig
And for make certifictes and config file for more users you can use this script: OVPNclient
OpenVPN server on Mikrotik with IOS13 client
Mikrotik OS6.47
Generate a Self-Signed CA certificate
/certificate add name=mt.ca common-name=mt.ca key-usage=key-cert-sign,crl-sign trusted=yes
/certificate sign mt.caGenerate a certificate for the vpn server (mikrotik router), sign it and trust it.
/certificate add name=ovpn.server common-name=ovpn.server
/certificate sign ovpn.server ca=mt.ca
/certificate set trusted=yes ovpn.serverGenerate a certificate for the vpn client (ipad or phone) and sign it.
/certificate add name=iosvpn.client common-name=iosvpn.client
/certificate sign iosvpn.client ca=mt.ca
/certificate set trusted=yes iosvpn.clientExport CA certificate
/certificate export-certificate mt.caExport client certificate to pcks12 file type (required for ios)
/certificate export-certificate iosvpn.client export-passphrase=12345678 type=pkcs12Exported client key pair is now in files with the filename cert_export_iosvpn.client.p12
Import it to OpenVPN connect with iTunes
cert_export_mt.ca.crt
Content of this file has to be placed at the end of .ovpn config file
.ovpn configuration file for IOS
client
dev tun
proto tcp #### Mikrotik uses TCP only
remote mynetname.net ### or IP address
port 1194 ####If you use defult port
resolv-retry infinite
nobind
persist-key
persist-tun
tun-mtu 1492
mssfix 1400
auth SHA1
auth-user-pass
verb 5
;comp-lzo ###(disable compression)
remote-cert-tls server
cipher AES-256-CBC
redirect-gateway def1 ### ios wont work without this
;remote-gateway 192.168.6.1
;dhcp-options DNS .8.8.8.8
;route 192.168.6.0 255.255.255.0 192.168.6.1
<ca>
-----BEGIN CERTIFICATE-----
### CONTENT OF mt.ca.crt FILE ###
-----END CERTIFICATE-----
</ca>
Save as iosclient.ovpn and import to OpenVPN connect on ios
Mikrotik OpenVPM server config
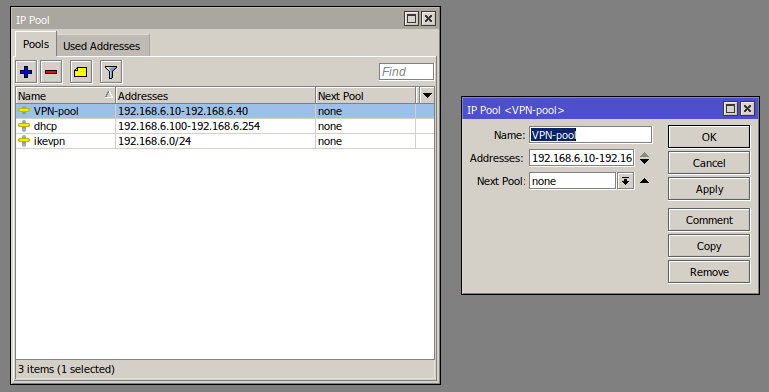
/ip/pool
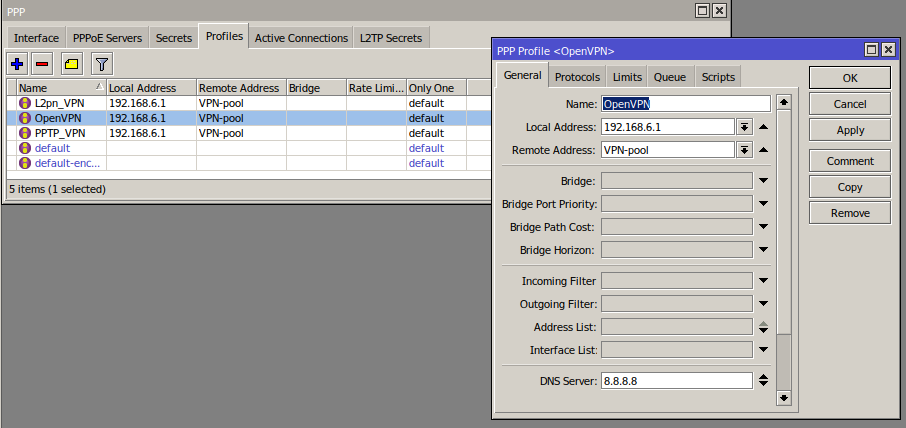
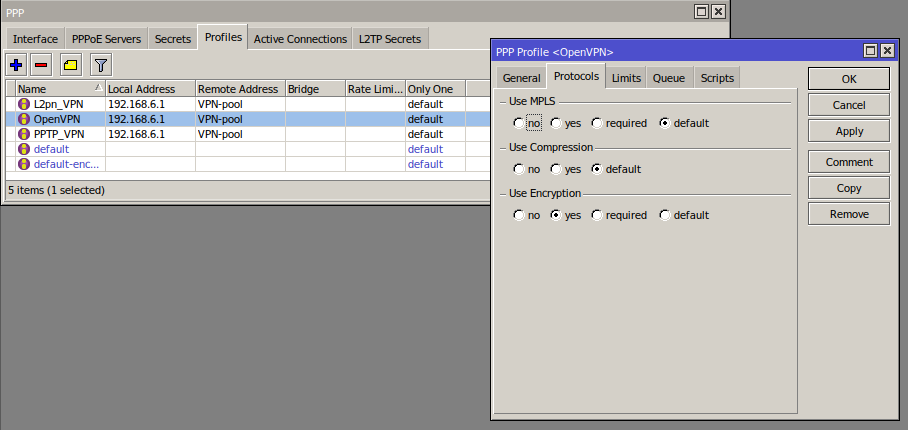
/ppp/profile
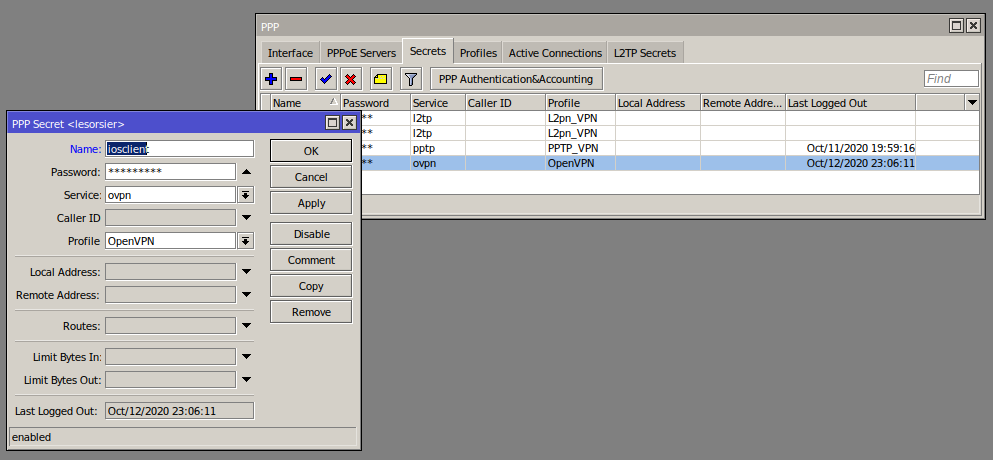
/ppp/secrets
/ppp
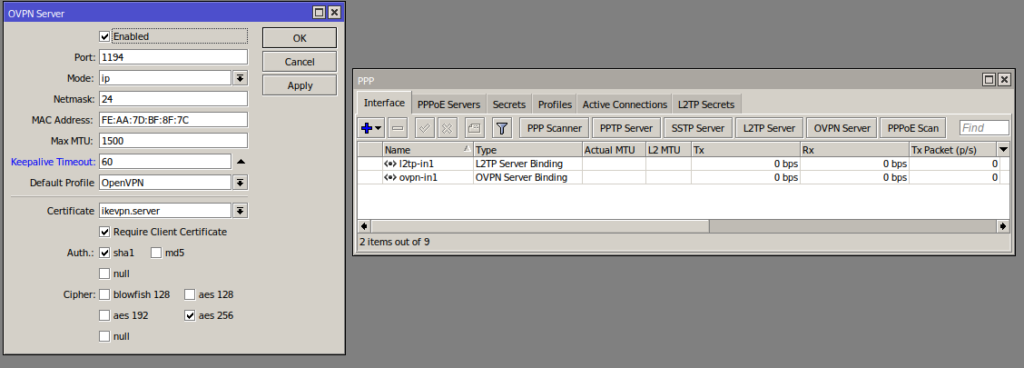
Open TCP port 1194 on firewall
/ip firewall filter add action=accept chain=input comment="allow OpenVPN" disabled=no dst-port=1194 protocol=tcp